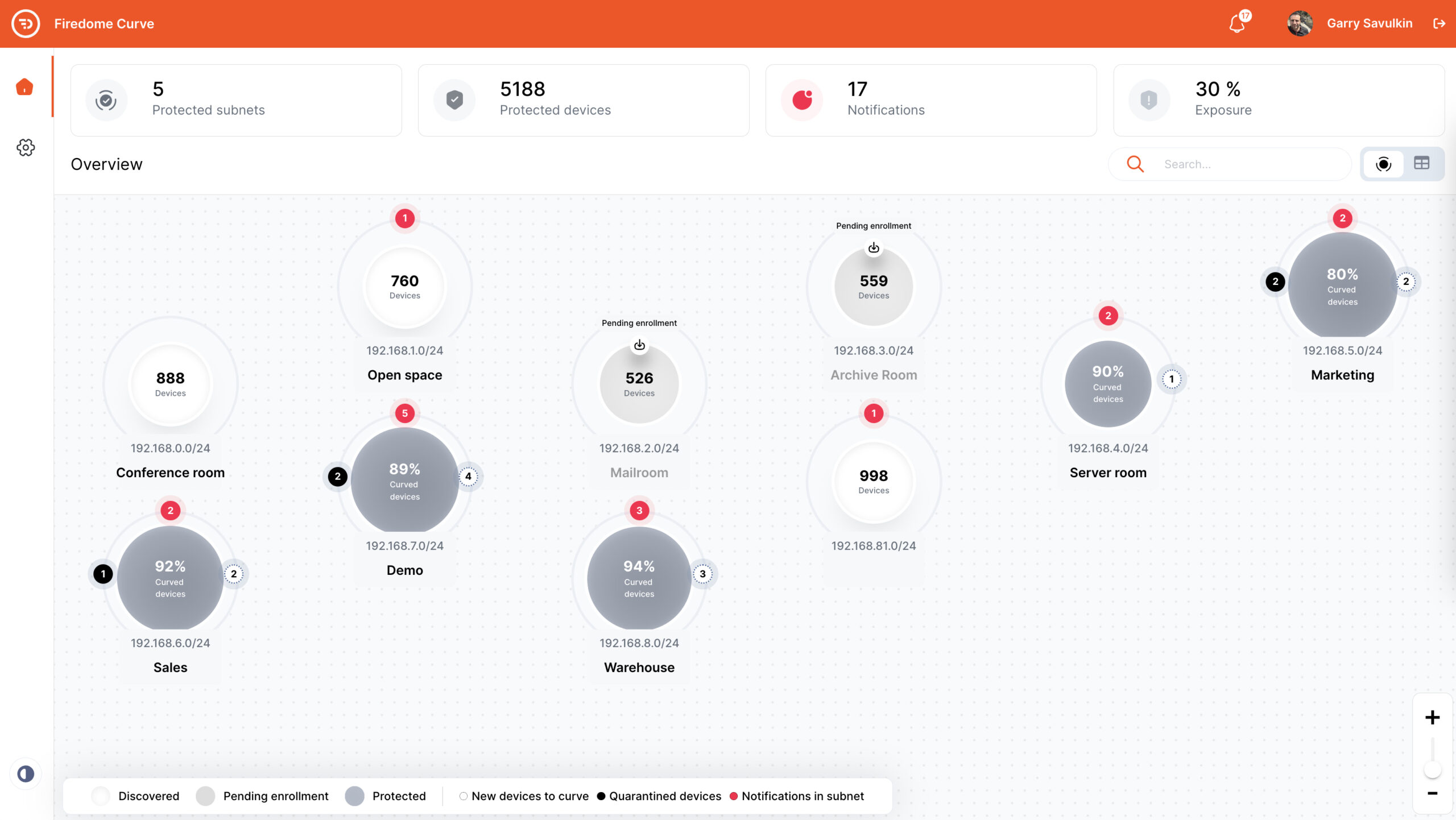
Firedome Curve™ enhances NDR solution ROI by replacing hardware appliance usage with innovative security features.
It utilizes network traffic metadata, deep packet inspection, and proactive scanning to optimize security while conserving computational resources.
Rapid deployment in days and minimal maintenance ensure unmatched ease of use.